Friday, March 27, 2009
It (still) hurts like hell
I think most people would never come close to understanding this kind of pain, which would be good if this were true... I'm grateful to God really for Yifen who really does love and know me, and I'm sure my sister-in-law does too for my brother. But even with the many people around who know about this and show concern, I believe the only one who can come close to understanding this would be my brother only.
Which is why I get quite frustrated when people come and say "Oh, you should keep trying to contact her. See, your mum is so hurt." or "It's only right to keep trying because we need to honour our parents."
Honouring father and mother I totally agree with. And that's because that is what God (or Christ) wants. But all this time thrashing it out in my mind what I still can't figure out is: why does it mean for me to honour her? Definitely far more than just fulfilling obligations/duty, but what I wish to do is exactly what's not possible now counting what's happened/happening. Totally frustrating...
Still much more floating around in my head, and after so long a time of thinking heh. But all still in a mess..
Tuesday, March 24, 2009
HP SWFScan Static Code Analysis Tool for Flash
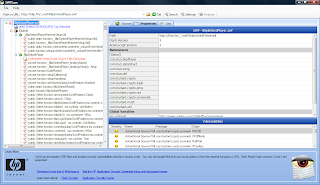
HP has released SWFScan, a free static code analysis tool for Flash. It does decompiling and static code analysis for a pretty huge list of vulnerabilities in Flash. Supports up to ActionScript 3.
Using it is easy: point it to the flash file, click on "Get" to retrieve and decompile, then click on "Analyse" to well...Analyse the source code :)
Decompiled source codes can be saved, and a HTML vulnerability report can be generated too after analysis.
FAQ
http://www.communities.hp.com/securitysoftware/blogs/spilabs/archive/2009/03/20/hp-swfscan-faq.aspx
Blog post
http://www.communities.hp.com/securitysoftware/blogs/spilabs/archive/2009/03/20/exposing-flash-application-vulnerabilities-with-swfscan.aspx
Download
Wednesday, March 18, 2009
ProxyStrike!
 Another tool to try out!
Another tool to try out!ProxyStrike is an active Web Application Proxy, is a tool designed to find vulnerabilities while browsing an application. It was created because the problems we faced in the pentests of web applications that depends heavily on Javascript, not many web scanners did it good in this stage, so we came with this proxy.
Right now it has available Sql injection and XSS modules. Both modules are designed to catch as many vulnerabilities as we can, it's that why the SQL Injection module is a Python port of the great DarkRaver "Sqlibf". The XSS module is made by us, using our library Gazpacho (soon will be released as standalone tool).The process is very simple, ProxyStrike runs like a passive proxy listening in port 8008 by default, so you have to browse the desired web site setting your browser to use ProxyStrike as a proxy, and ProxyStrike will analyze all the paremeters in background mode. For the user is a passive proxy because you won't see any different in the behaviour of the application, but in the background is very active. :)
Features:
- Plugin engine (Create your own plugins!)
- Request interceptor
- Request diffing
- Request repeater
- Automatic crawl process
- Save/restore session
- Http request/response history
- Request parameter stats
- Request parameter values stats
- Request url parameter signing and header field signing
- Use of an alternate proxy (tor for example ;D )
- Sql attacks (plugin)
- Server Side Includes (plugin)
- Xss attacks (plugin)
- Attack logs
- Export results to HTML or XML
Wednesday, March 11, 2009
HOWTO: Determining the day of the week from the date in Microsoft Logparser
MOD(DIV(TO_INT(TO_DATE(DateTime)), 86400), 7)
logparser -i:csv -o:datagrid "SELECT DISTINCT TO_DATE(DateTime), MOD(DIV(TO_INT(TO_DATE(DateTime)), 86400), 7) FROM datetest.csv"
logparser -i:csv -o:datagrid "SELECT DISTINCT TO_DATE(DateTime), Day USING CASE MOD(DIV(TO_INT(TO_DATE(DateTime)), 86400), 7) WHEN 0 THEN 'SAT' ELSE CASE MOD(DIV(TO_INT(TO_DATE(DateTime)), 86400), 7) WHEN 1 THEN 'SUN' ELSE CASE MOD(DIV(TO_INT(TO_DATE(DateTime)), 86400), 7) WHEN 2 THEN 'MON' ELSE CASE MOD(DIV(TO_INT(TO_DATE(DateTime)), 86400), 7) WHEN 3 THEN 'TUE' ELSE CASE MOD(DIV(TO_INT(TO_DATE(DateTime)), 86400), 7) WHEN 4 THEN 'WED' ELSE CASE MOD(DIV(TO_INT(TO_DATE(DateTime)), 86400), 7) WHEN 5 THEN 'THU' ELSE 'FRI' END END END END END END AS Day FROM datetest.csv"
